 Over the last 12 months, has your dns provider indicated significant growth in the number of queries they record for your domains?
Over the last 12 months, has your dns provider indicated significant growth in the number of queries they record for your domains?
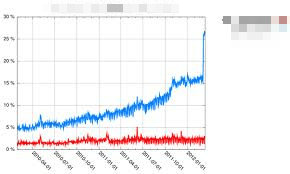
I recently noticed comments on various provider forums regarding dns usage for domains that had experienced meteoric rises in usage and thus charges. People were asking why their few thousand query a month domains were experiencing growth in the 100’s of thousands of queries. Most premium DNS providers, at least to some extent have a pay-per use model. For many you sign up for a specific amount of queries per month or year. You can incur fairly significant ‘overage’ fees when exceeding these agreed amounts.
The last 12 months or so of dns growth you’ve been experiencing may not at all be down to the growth in your bushiness. I compare what some of the pay-per-use dns companies are doing is akin to the click through fraud problem in the ad world. Whilst the dns companies themselves are not responsible, some are apparently being complacent in protecting their users and charging them for it. If you signed up for a dns service contract a year ago, you could now be facing significant overage charges with some providers due to traffic that isn’t even legitimate.
The reason? Criminals, essentially. A very common form or internet attack at the moment is to use a dns server to attack another server. A computer makes a small DNS query to your server with a forged ‘from’ address. They make a type of query that normally illicits quite a big response. Because the source address has been forged, the dns server sends the reply back to the forged address, the target of the attack. A very small query from the client results in a much bigger response being sent to the target. Distribute this same query to a large pool of dns servers on the internet and you have a significant weapon. In this way, with surprisingly few resources, the attack is amplified to something that can overwhelm other servers or even entire networks. If you’ve looked at your dns logs recently and seen 1000’s of ANY requests for your domains, you’ve likely unwittingly been a part of these attacks.
For pay per use clients, the recent growth in this type of attack is the cause of some significant ‘overage’ invoices or increases in fees. The cynic in me wonders if the relationship between malware and antivirus providers is akin to DNS amplification attacks and DNS providers. I’m sure a few coffers have been swelled over the past year as a result, so are the dns companies turning a blind eye to the issue? Some have been vocal in solutions, BCP 38 for example, but it’s generally a problem to solve elsewhere rather than the dns provider themselves. Others have taken a more proactive response implementing rate limiting and log correction for example.
When selecting a premium dns provider ask them what their policy on fraudulent queries is, just as you would if you selected a pay-per-click advertising agency. Don’t forget! It could cost you more than you think…